Drupal 7 sites are still getting hacked and infected with malware
‘Tis the season to be cracking.
In the webhosting business we’re used to seeing an increase in attacks during the holidays, as most people by then are busy with real life. If you’re a cracker though, this is your favorite time of the year.
I recently noticed that a lot of hosts were scanning my servers looking for Drupal and WordPress installations. Nothing new under the sun surely, but when every scan follows the same pattern, well then I’m intrigued.
[25/Mar/2016:07:59:43 +0100] "GET / HTTP/1.0" 403 [25/Mar/2016:07:59:48 +0100] "GET / HTTP/1.1" 403 [25/Mar/2016:07:59:53 +0100] "GET /CHANGELOG.txt HTTP/1.1" 403 [25/Mar/2016:07:59:57 +0100] "GET / HTTP/1.1" 403 [25/Mar/2016:08:00:02 +0100] "GET /readme.html HTTP/1.1" 403
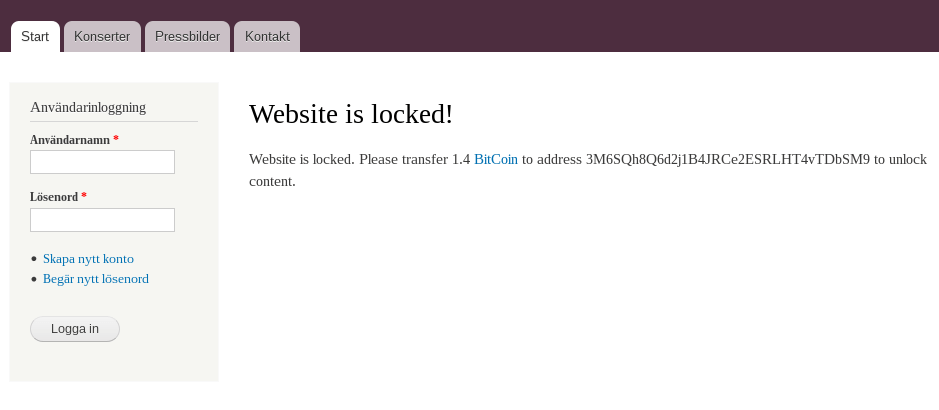
Website is locked, will accept bitcoins.
When I visited a few of the hosts performing the scan, I always ended up on a Drupal 7 based installation. All of them showing the exact same bitcoin demand (using the same bitcoin address) as shown on the image to the right.
I’m not entirely sure what kind of malware these sites are getting infected with. The demand itself suggest ransomware, but it doesn’t seem to encrypt data as pages still load fine, and I could even register a new account, suggesting that the Drupal backend still does work.
Some of the sites had even removed the “bitcoin demand” page, but they were still performing vulnerability scans. That is what happens when you host malware, even though as far as you can tell, the only problem was an annoying piece of text on your homepage (which you aptly fixed). The reason I’m sure the site owners did nothing besides a little editing is the fact that they’re still running vulnerable Drupal installations.
Remember the “CHANGELOG.txt” requests? That file will actually tell the attacker which version of Drupal you’re running. By using Drupal prior to version 7.32 you’re unfortunately exposed to the biggest security flaw in Drupal’s history. As a matter of fact, any cracker out there can own your site with a minimum of effort. This vulnerability: SA-CORE-2014-005, got labeled the DRUPAL-OPCALYPSE, back in 2014!
I’ve investigated the version number of every compromised Drupal installation I could find, and unsurprisingly, not a single one had implemented the before mentioned patch. In other words, this is (most likely) not a new Drupal exploit but a consequence of people not understanding why security updates always need to be applied.
As for the malware used, I would not be surprised if does not only detect vulnerable Drupal installations, but also has the ability to infect them on the fly. I don’t have access to a compromised site so I’m not familiar with the damage it does or the technique it uses, but your best response by now would be to wipe everything clean. Yep, that’s really the only reliable solution, delete everything and remember to apply security patches the next time around.
Happy holidays!
