Email service providers should kill off the bitcoin extortion scam
Like everyone else with an email address, I’ve been receiving these bitcoin extortion messages for months. I’ve also observed with ever greater dissatisfaction as scammers raked in tens of bitcoins within a week. What especially annoys me is not so much that people are falling for this scam, but that email service providers are simply looking the other way.
From what I’ve observed, the most successful variants of the scam campaign takes advantage of existing data breaches to combine your email address with a previously used and compromised password: A Bitcoin extortion email released from quarantine for your viewing pleasure.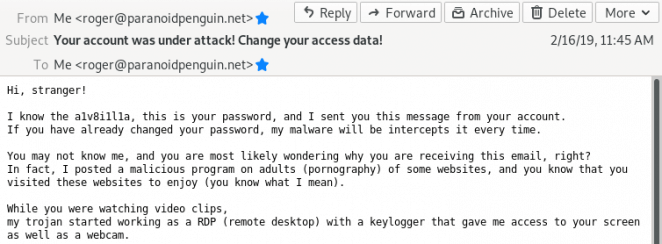
I don’t really care how trivial it’s technically to both perform and reveal this scam because those extortion messages have no business ending up in your users’ inboxes. I find sysadmins who argue that this extortion scam wouldn’t be a problem if their users just weren’t so darn stupid, to be both incompetent and useless.
I believe those aforementioned sysadmins would be better off by spending some time doing their actual job. Why not replace those old email servers that EOL’d back in 2013. And while you’re at it, I’d also like to suggest the following search phrase between coffee breaks: SPF+DKIM+DMARC.
Implementing email security standards makes it easy to reject and quarantine these bitcoin extortion messages before they ever reach the end user:
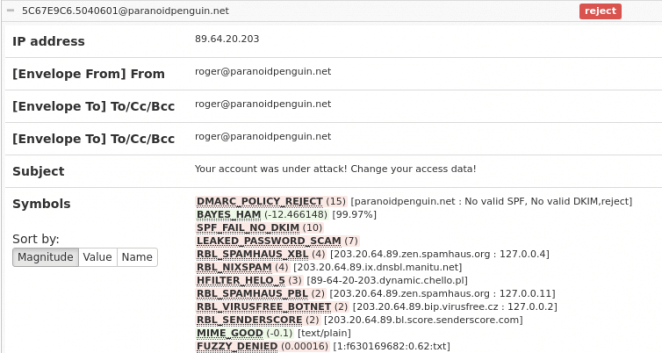
No valid SPF or DKIM caused this extortion mail to be rejected. Yup, it’s really that easy.
I would recommend calling your email service provider if your mailbox is getting flooded with these extortion scams (without them being labeled as spam) and ask them to get their shit together. Or even better yet, find an email service provider that actually cares about your privacy and security.
