Malicious bots sending siteru as the HTTP referer
I’ve received a few hundred requests originating from bots setting site.ru as their referrer. These attacks are scanning for compromised WordPress installations and PHP based shells and backdoors. The attacking IP’s belong to compromised hosts and websites from service providers around the world.
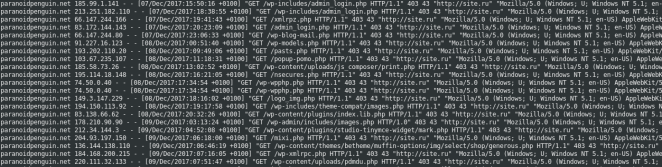
Probes using site.ru as the HTTP referer.
Who owns site.ru?
The host is currently unavailable, but according to the Internet Archieve it was previously running a news portal credited to a company named Inforos. The domain has enabled WHOIS privacy so no further information was available regarding its owner. However, the current nameserver records for site.ru do still show a connection to Inforos.
dig site.ru ns +short ns2.inforos.ru. ns1.inforos.ru.
Why send a fake HTTP referer?
The technique is called spamdexing and it’s used to drive large volumes of traffic to a specific URL or domain. However, the advertising benefits of attaching your domain to this kind of hostile activity seem dubious at best. It’s entirely plausible that someone unrelated to the site.ru domain is behind the traffic.
Thanks for all the fish
Anyhow, my favorite bots are always those that uniquely identify themselves. Let’s simply use the HTTP referer to block every single one of these requests.
<IfModule mod_rewrite.c>
RewriteCond %{HTTP_REFERER} site\.ru [NC]
RewriteRule ^(.*)$ - [L,R=403]
</IfModule>
Site.ru blocklist
You’ll find my ever growing collection of site.ru bots available from the following repository.
