Self-hosting security challenge
If you’re a geek like me then you probably enjoy spending your time hardening and optimizing your servers to support modern security standards and policies. If so, I’d like to share my favorite online resources and encourage you to take up the challenge of beating paranoidpenguin.net.
Prerequisites
To be able to get by all the challenges, you’ll need to make sure that your service and infrastructure providers are supporting modern standards as well. This might prove more difficult than you might expect. Here is a shortlist of what you need:
- A top-level domain with DNSSEC support.
- Nameservers with support for TLSA and CAA records.
- IPv4 and IPv6 networking.
To beat the challenges I’m offering, you’ll need to self-host both your website and email service. As far as I’m aware, no commercial service providers are currently able to pass all the tests.
I’m aware that some of these tests are overlapping, but in my opinion, it never hurts to get a second opinion.
Disclaimer
It’s worth mentioning that the level of hardening required to pass these challenges will remove support for older (and insecure) clients. In other words, deploy to enterprise entirely on your own volition. I would also like to mention that I have no financial interest in, or other involvement with any entity discussed in this article.
Challenge 1: Get an A+ rating from SSL Labs
So you have managed to install an SSL certificate on your website? Well done, but how much time did you spend on configuring protocols and cipher suites. Qualys’ SSL server test will answer that question for you.
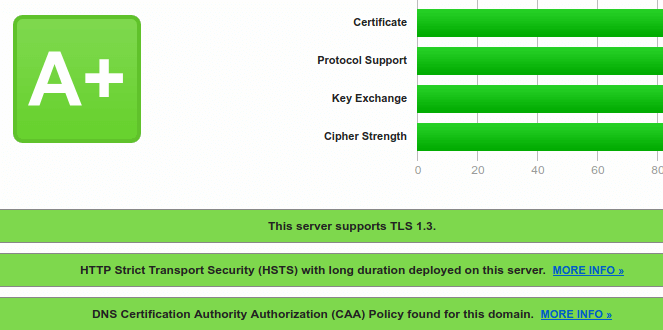
SSL report for paranoidpenguin.net from Qualys’ SSL Server Test.
Challenge 2: Get an A+ rating from Security Headers
Does your website have a Content Security Policy (CSP) to detect and mitigate cross-site scripting (XSS) and code injection attacks? If not, I would recommend implementing one. It’s easy to do and it will serve as a flexible and powerful defense mechanism against common attack vectors.
CSP makes it possible for server administrators to reduce or eliminate the vectors by which XSS can occur by specifying the domains that the browser should consider to be valid sources of executable scripts. A CSP compatible browser will then only execute scripts loaded in source files received from those allow-listed domains.
Source: developer.mozilla.org
SecurityHeaders.com will analyze your HTTP response headers, including your Content Security Policy, and recommend improvements where applicable.
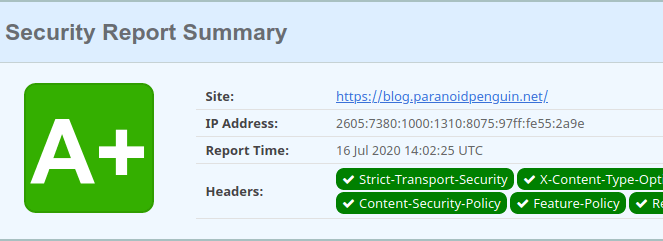
Security report for paranoidpenguin.net from Security Headers.
Challenge 3: Get on Internet.nl’s Hall of Fame page
Internet.nl helps you to check whether your internet is up to date. Do your website, email and internet connection use modern and reliable Internet Standards? And if they don’t, what can you do about it?
If you can score 100% on Internet.nl’s website and email test, then you’re eligible to join (currently) 705 other domains on their Hall of Fame page. I hope you’re warmed up because the time has come to put your sysadmin glasses on.
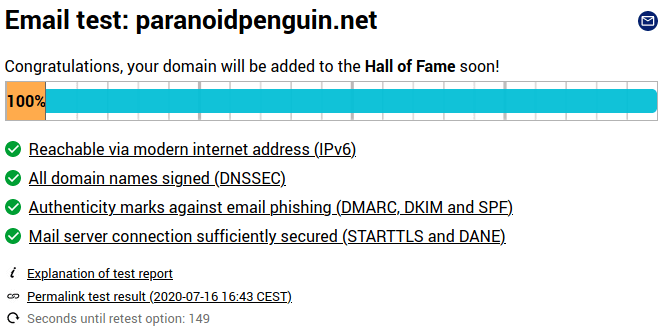
Website and email test results for paranoidpenguin.net with Internet.nl.
Challenge 4: Check all the boxes with Hardenize
Hardenize provides a managed service that combines host and web site discovery, network and security configuration analysis, and certificate monitoring in one package.
I saved the best (in my opinion) for the last. Hardenize is a service I recently discovered that offers a complete configuration check of your domain, web, and email services. It was Hardenize that convinced me to take another look at, and implement MTA Strict Transport Security (MTA-STS) after I had initially discarded the mechanism.
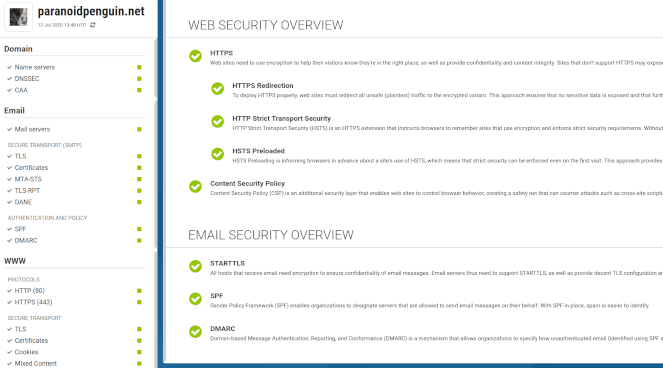
Paranoidpenguin.net checking all the right boxes with Hardenize.
Show me your report card
How did you score, and were you able to defeat paranoidpenguin.net? If so, I would love to know. Either way, if you made an effort to implement some of these security standards and policies, then we all win.
If you don’t self-host your web and mail servers then feel free to run these tests against your service providers instead. Or maybe give your friendly neighborhood security expert a run for their money. The results might surprise you.
