HTTPS for WordPress on a Raspberry Pi 2
So you’re hosting your own WordPress blog on a Raspberry Pi 2 and want to join the HTTPS everywhere movement to ensure optimal privacy for your visitors. That’s great, but what kind of performance penalty can you expect as CPU intensive tasks are hardly a favorite with the RPi2. Is the extra computational cost of encrypting data and doing handshakes going to significantly slow down your site?
Well, you can probably answer that question yourself as your browser has just loaded this page over a secured TLS connection. Though WordPress can still serve static content generated by my caching plugin, there is no hiding the additional burden of doing handshakes and encryption. On my RPi2, the extra overhead is between 500 – 1000ms depending on latency.
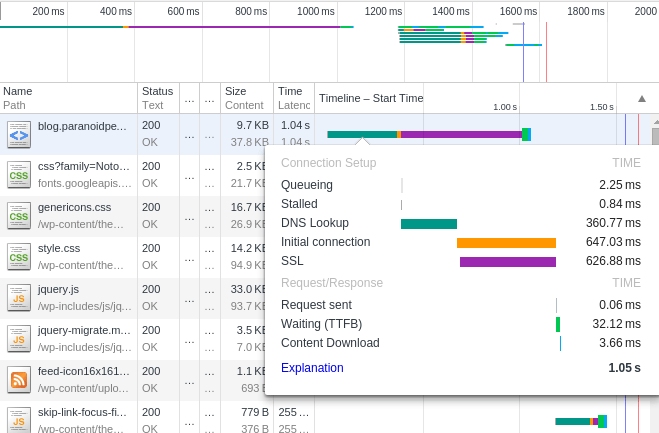
A network timeline visualizing the additional load after implementing encryption.
Server details:
Slackware ARM current Apache 2.4.x OpenSSL 1.0.2 Cipher Suite: Adhering to Mozilla's Server Side TLS Guidelines (intermediate profile).
RPi2 configuration:
arm_freq=1000 sdram_freq=500 core_freq=500 over_voltage=2
Limitations and issues with my setup:
- Slackware ARM is a soft float distribution focused more on legacy compatibility than performance gain on modern arm devices. With OpenSSL that unfortunately gives me the short end of the stick.
- I’m using a 4096 bit private key, which is probably just a waste of CPU cycles. I’m not sure what I was thinking at the time, but I’ll definitely “downgrade” to a 2048 bit key next week.
- I’m doing too many TLS handshakes. Perhaps it’s finally time to write my own WordPress theme and do away with all those excess requests.
RPi2 OpenSSL benchmark
$ openssl speed ecdh
op op/s
160 bit ecdh (secp160r1) 0.0037s 271.7
192 bit ecdh (nistp192) 0.0053s 188.9
224 bit ecdh (nistp224) 0.0069s 144.6
256 bit ecdh (nistp256) 0.0093s 107.1
384 bit ecdh (nistp384) 0.0222s 45.0
521 bit ecdh (nistp521) 0.0509s 19.7
163 bit ecdh (nistk163) 0.0083s 120.8
233 bit ecdh (nistk233) 0.0157s 63.5
283 bit ecdh (nistk283) 0.0292s 34.2
409 bit ecdh (nistk409) 0.0670s 14.9
571 bit ecdh (nistk571) 0.1557s 6.4
163 bit ecdh (nistb163) 0.0089s 112.3
233 bit ecdh (nistb233) 0.0175s 57.1
283 bit ecdh (nistb283) 0.0327s 30.5
409 bit ecdh (nistb409) 0.0772s 13.0
571 bit ecdh (nistb571) 0.1791s 5.6
So after all is said and done, was it worth sacrificing speed for encryption? Only time and Google Search Console will tell :-)
My certificate is signed by Let’s Encrypt, get yours today for free!
