How did a subdomain on cancer.org end up serving porn?
A few days ago I discovered several referral spam links to the domain servicematch.cancer.org in my server logs. Spam referrals are usually a part of some blackhat SEO campaign used to generate traffic, and if possible, get the URL listed on a website’s public statistics page.
Content warning: This article contains mildly sexually explicit text and images.
However, since the domain belonged to The American Cancer Society, I decided to investigate further. To my surprise, the subdomain was hosting porn content in an attempt to drive traffic to an external website.
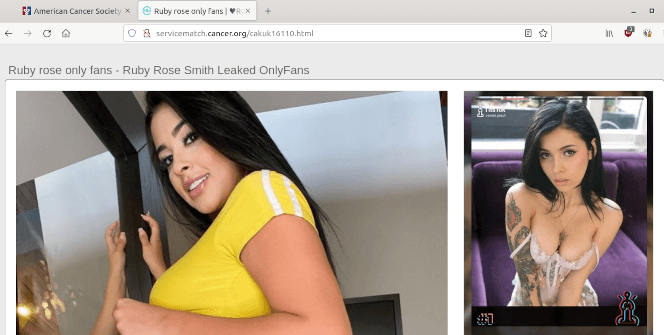
The hijacked subdomain is seen pointing to the attacker’s Azure resource.
This is an unfortunate situation, and the potential for further misuse is substantial. However, if the party responsible for managing the domain’s DNS zone file had done their job, it could never have happened.
The quick explanation is that the servicematch.cancer.org domain was pointing to a deprovisioned Azure resource. If an organization neglects to remove DNS records for deprovisioned resources, it opens a possibility for an attacker to provision another Azure resource using the same fully qualified domain name. As was the case with the hijacked subdomain belonging to The American Cancer Society.
Before the dangling DNS records eventually got purged, the following result was returned when querying servicematch.cancer.org:
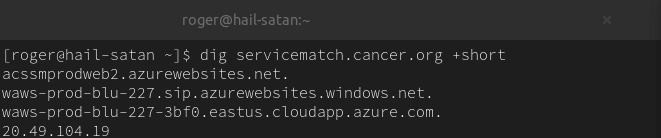
The Azure resource shown in the DNS answer section above is still online by the time this article got posted. The subdomain record, however, has been deleted.
Microsoft classifies subdomain takeover as a high-severity threat. Additionally, Microsoft also provides documentation on how to mitigate the threat: Prevent dangling DNS entries and avoid subdomain takeover.
As mentioned, the dangling DNS entries pointing to the attacker’s resource are now removed. Hopefully, The American Cancer Society will keep a closer watch on their almost 400 subdomains in the future and not blindly rely on DevOps, because this was a mess.
And by looking at the DNS history for the subdomain, it looks like it was hijacked the same day as it was dropped. That only goes to show how widespread these attacks are.
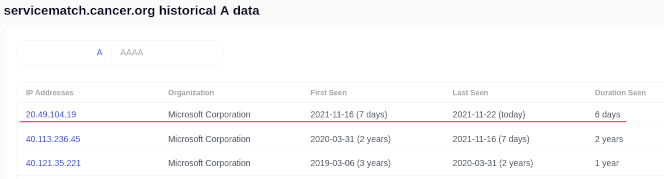
DNS record history, showing the timeframe for the hijack.
And even during that short window of time, Bing managed to index a good number of pages hosted under the subdomain. I guess Bing is skilled at crawling Azure resources. Anyhow, I suspect someone will have a busy time filling out page removal requests with Bing Webmaster Tools.
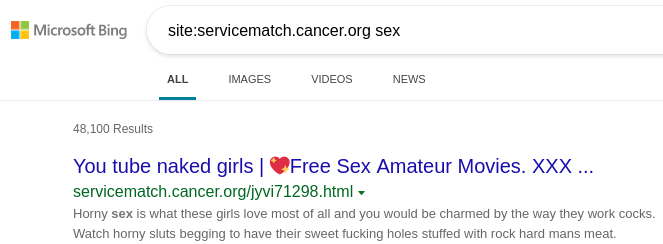
Bada Bing!
#DevOops
