The Mozilla Observatory has become an embarrassment
I find great value in much of Mozilla’s technical documentation and resources. However, the current state of the Mozilla Observatory can hardly be described as anything other than an embarrassment. I believe it’s high time the people behind the project start to eat their own dog food.

This site uses an untrusted or invalid certificate (website uses a Let’s Encrypt certificate).
Let’s Encrypt certificates are invalid?
When the Mozilla TLS Observatory service tries to validate the certificate chain for paranoidpenguin.net, it discovers the Let’s Encrypt root certificate called ISRG Root X1. It then erroneously reports back that the ISRG Root X1 is not trusted by Mozilla.
As a side note, Let’s Encrypt has frequently warned about the planned DST Root CA X3 expiration that would take place on September 30, 2021. My immediate guess would be that not everyone got that particular memo.
To retrieve the more detailed and technical information, we can ask the tls-observatory.services.mozilla.com API server directly for a report:
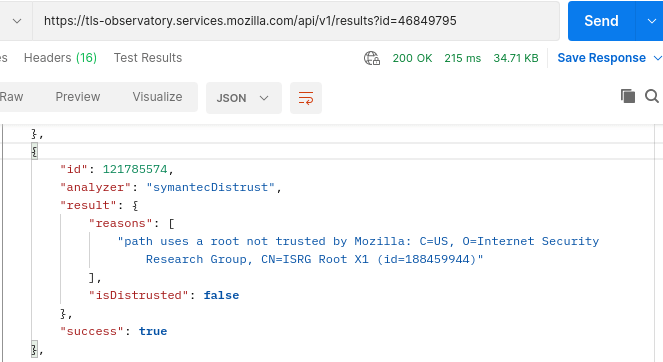
Result: path uses a root not trusted by Mozilla: CN=ISRG Root X1.
Mozilla certainly does trust Let’s Encrypts root certificate ISRG Root X1. However, that assumes the software stack has been updated sometime since 2016. Unfortunately, the infrastructure behind the Mozilla TLS Observatory seems to be effectively unmaintained.
TLS 1.3 - The unsupported protocol
We’re not done yet. If you rely on the Mozilla SSL configuration generator to deploy a modern and secure configuration for your SSL webserver, well, then you might be in for another surprise. Mozilla’s modern SSL configuration only works for clients that support TLS 1.3.
The Mozilla HTTP Observatory does not support TLS 1.3 and will end up stuck with the message “SCAN IN PROGRESS” while your webserver log fills up with the following notices:
[info] 61795#61795: *2 SSL_do_handshake() failed (SSL: error:14209102:SSL routines:tls_early_post_process_client_hello:unsupported protocol) while SSL handshaking, client: 2620:101:8030:74::1:16, server: [::]:443
[info] 61795#61795: *3 SSL_do_handshake() failed (SSL: error:14209102:SSL routines:tls_early_post_process_client_hello:unsupported protocol) while SSL handshaking, client: 2620:101:8030:74::1:16, server: [::]:443
[info] 61795#61795: *4 SSL_do_handshake() failed (SSL: error:14209102:SSL routines:tls_early_post_process_client_hello:unsupported protocol) while SSL handshaking, client: 2620:101:8030:74::1:16, server: [::]:443
[info] 61795#61795: *5 SSL_do_handshake() failed (SSL: error:14209102:SSL routines:tls_early_post_process_client_hello:unsupported protocol) while SSL handshaking, client: 2620:101:8030:74::1:16, server: [::]:443
What is that Mozilla service running
The public-facing web servers are exposing their software version in the servers’ response headers. The response header field Server: nginx/1.10.3 (Ubuntu) reveals both the webserver version and the underlying operating system. Based on that information, it’s likely that the services are running on Ubuntu 16.04 LTS (Xenial Xerus) servers. That would explain the lack of support for modern web security standards.
The Mozilla Observatory is a project designed to help developers, system administrators, and security professionals configure their sites safely and securely. With that goal in mind, you simply have to do a far better job. Fix it or take it down. Never deploy and forget.
Coincidentally, I happen to know a system administrator willing to offer a helping hand ;)
