Plausible Analytics review – Browser fingerprinting and CNAME cloaking
For the last few weeks, my feeds and federated timelines have been filled with absolutely brilliant marketing campaigns for Plausible Analytics, the new open-source privacy-focused website analytics tool. Plausible Analytics has enjoyed exponential growth and is frequently recommended by privacy-conscious voices in the FOSS community.
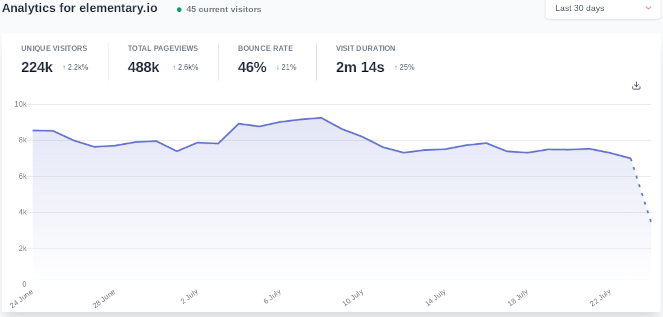
Plausible Analytics showing public visitor metrics for the elementary OS website.
So does Plausible Analytics deliver on its promise to provide an ethical privacy-friendly alternative to Google Analytics? Let’s have a closer look.
GDPR compliance by default
Plausible Analytics claims to be compliant with GDPR, CCPA, and PECR out of the box. Allegedly, it’s not necessary to ask for and obtain user consent as no personal data is ever being collected.
Plausible Analytics does however admit that it collects your user-agent and IP address to uniquely identify your visit. Additionally, it stores information about your browser, operating system, device type, and location (based on your IP address). Even if the stored personal data is being anonymized (and not pseudonymized which sounds more likely), the data is still being processed.
If you’re familiar with GDPR, then you’re likely aware that it certainly covers collecting of online identifiers, such as IP addresses, and browser characteristics used for fingerprinting.
Another issue I came across when signing up for their service was that Plausible Analytics doesn’t provide their customers with a GDPR data processing agreement (DPA). When you, the website owner, allows a third party to collect and process personal data, you’re required to sign a DPA to be GDPR compliant.
Privacy-friendly website analytics
In my opinion, privacy-friendly should be more than a buzzword used to throw shade at Google Analytics. Here are a few key points that I attribute to being privacy-friendly (none of which are adhered to by Plausible Analytics):
- Ask users for their consent before tracking.
- Allow users who don’t want to be tracked to opt-out.
- Respect users providing a Do Not Track (DNT) header.
- Don’t disguise your tracker as a first-party resource to avoid ad-blockers.
Being privacy-friendly is also about respecting one’s right to choose what data to share, and with whom. Plausible Analytics seems to think that it’s alright to make that choice on your behalf and I wholeheartedly disagree.
CNAME cloaking
This abysmal technique remains ever popular with unethical advertisers as an effective countermeasure against ad-blockers. The technique effectively disguises the third-party tracker as a first-party resource by having the website owner pointing a subdomain to the third-party server using a CNAME record.
Plausible Analytics are at least upfront about why they deploy CNAME cloaking, as explained in their documentation:
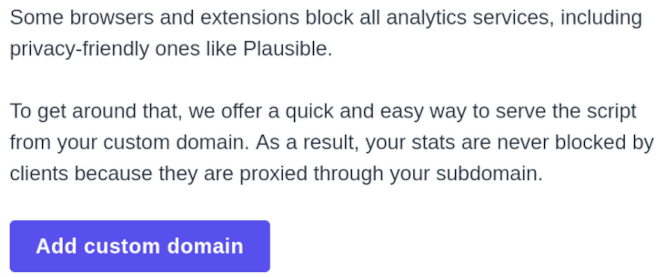
Plausible Analytics documenting how to defeat ad-blockers.
What, some people are trying to block your privacy-friendly tracker? Now we can’t have that, tracking absolutely everyone gives Plausible Analytics a competitive edge against Google Analytics.
How does CNAME cloaking work?
An excellent question, but first we need to understand exactly what makes CNAMEs special by design and implementation as according to rfc1034.
A CNAME RR identifies its name as an alias, and specifies the corresponding canonical name.
When a name server fails to find a desired RR in the resource set associated with the domain name, it checks to see if the resource set consists of a CNAME record with a matching class. If so, the name server includes the CNAME record in the response and restarts the query at the domain name specified in the data field of the CNAME record.
Let’s see how it works by using the domain markosaric.com as an example. The domain is owned by Marko Saric, digital marketing guru of team Plausible Analytics. The subdomain he uses to disguise the tracker is ms.markosaric.com. When performing a DNS query for ms.markosaric.com, we get the following response:
$ dig ms.markosaric.com
;; ANSWER SECTION:
ms.markosaric.com. 14400 IN CNAME custom.plausible.io.
custom.plausible.io. 300 IN A 46.101.161.209
As we can tell, the DNS resolver identifies ms.markosaric.com as an alias for custom.plausible.io. Additionally, because it’s a CNAME record, we also get the A record for custom.plausible.io which is pointing to 46.101.161.209.
When a browser requests the first-party resource for ms.markosaric.com, the same “DNS based redirect” takes place, and the tracker gets inserted from custom.plausible.io. However, because this happens at the DNS level, ad-blockers are unable to identify the tracker.
Let’s see how this dark magic repels uBlock Origin on Chromium after adding a custom filter to block the plausible.io domain.
! Custom uBlock Origin filter for plausible.io
||plausible.io^
The image below consists of two merged screenshots. The left side of the image shows how the custom filter fails to stop the tracker when CNAME cloaking is in effect. The right side of the image shows the same filter successfully blocking the tracking domain when accessed directly:
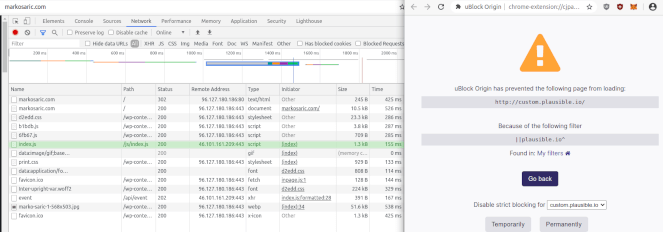
CNAME cloaking used to escape filtering from uBlock Origin on Chromium.
As shown above, the tracker (index.js) is being loaded from the remote IP address of 46.101.161.209, which resolves to custom.plausible.io. However, the script is not blocked and the harvesting of personal data is in full effect.
This technique is effective because uBlock Origin doesn’t have access to DNS queries and is entirely oblivious to the trick being pulled behind its back. I wouldn’t describe this approach as being either privacy-friendly or ethical.
How to block Plausible Analytics
Though intrusive, unethical, and annoying, CNAME cloaking can be defeated. I’ll scratch the surface with a few options that will help you to protect your privacy.
uBlock Origin on Firefox
You can easily block Plausible Analytics with uBlock Origin on Firefox by adding the filter I referenced earlier in this article. Firefox allows extensions (if given permission) to resolve domain names by exposing a DNS API. This allows uBlock Origin to identify and block disguised trackers:
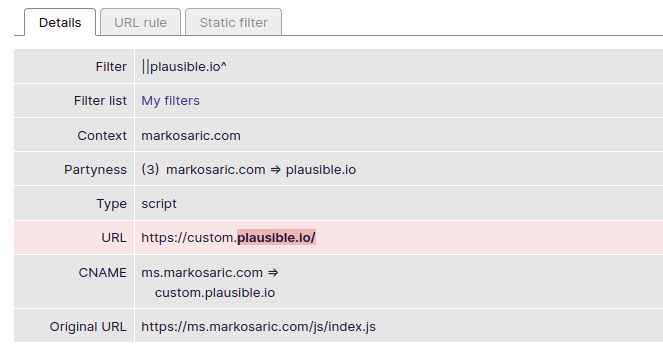
uBlock Origin using Firefox’s DNS API to expose and block CNAME cloaking.
dnscrypt-proxy
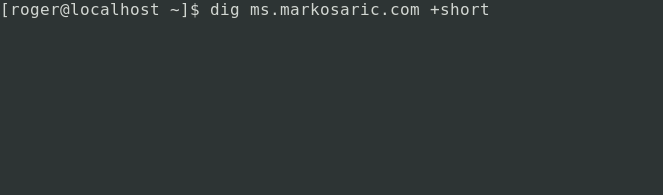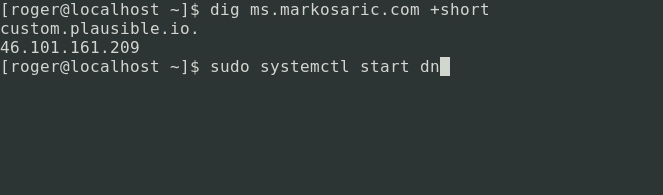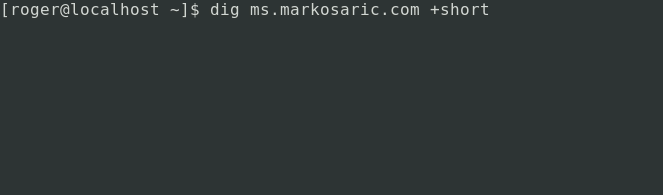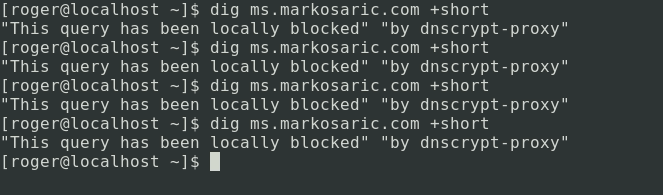
If you don’t want to use Firefox, or prefer to block Plausible Analytics on the DNS level, then you’ll need a tool that can scrub CNAME responses. The right tool for the job in my opinion is dnscrypt-proxy. The dnscrypt-proxy client’s domain blacklist provides support for CNAME blocking.
The following animated gif shows how dnscrypt-proxy can block the CNAME record containing the unwanted tracker.
Pretty neat huh.
Other options
Well there are a few, you could always:
- Block any IP address in use by custom.plausible.io with your firewall.
- Disable JavaScript in your browser (it will block the tracking, not the connection).
- Block the subdomains used for CNAME cloaking.
- Use a DNS service provider already blocking unwanted trackers.
- Ask Plausible Analytics to respect your right to privacy.
What does the FOSS say?
I’ll admit to being mildly amused and surprised that privacy-conscious people in the FOSS community are promoting this service. Even more surprising is the fact that they’re configuring CNAME cloaking for their websites. I mean, seriously, you can’t exactly argue ignorance in this matter.
Plausible Analytics is good at targeted marketing to the right people. However, I don’t personally believe that the product delivers on its promise. Open-source or not, the business model here is still to monetize personal data for profit however you may wish to dress it up.
