Joe Nobody tries to take down a crypto scammer
Annoying e-mail spam lures Joe Nobody out of his slumber to once again try to convince service providers to pull the plug on a scammer. Welcome to another installment of Joe Nobody VS world.
The plot
This scam is neither sophisticated nor something we haven’t seen before. However, it makes for an excellent demonstration case that illustrates how difficult it is to take down this sort of content. Let’s have a look at how it works, and expose the service providers that facilitate it.
The spam email
Earlier today I received an email from “Coinbase” <contact@letterspd[.]com> informing me that Coinbase needed additional information from me to comply with the latest SEC (The Securities and Exchange Commission) regulations.
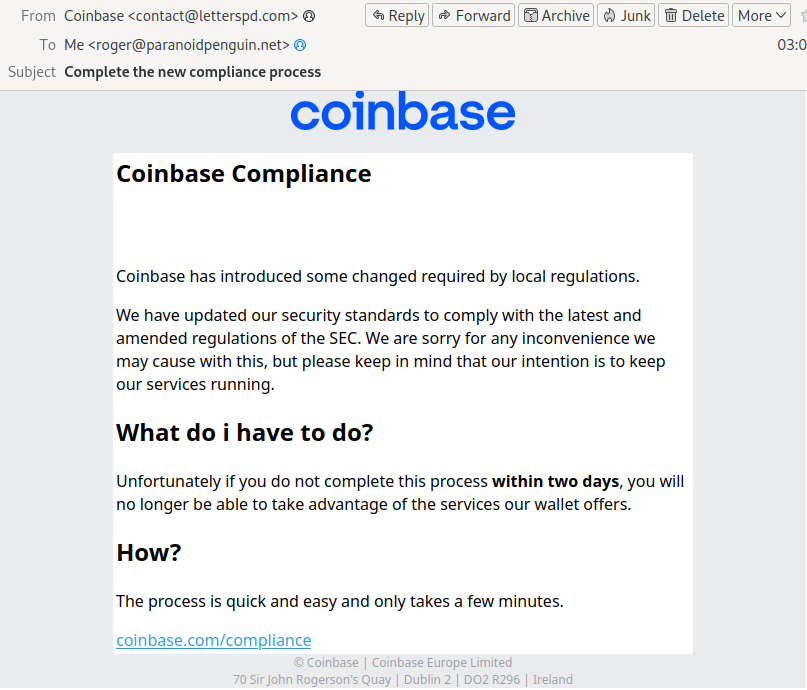
Not a bad scheme since SEC’s continuous legal filings against blockchain projects are frequently in the news. However, the design and the layout of the message leave much to be desired. Looking closer at the link masqueraded as coinbase[.]com/compliance reveals its true destination as pxlme[.]me/Sxv6cPZH
When looking at the email headers from the message, we can see where it originated from, and its journey to my inbox:
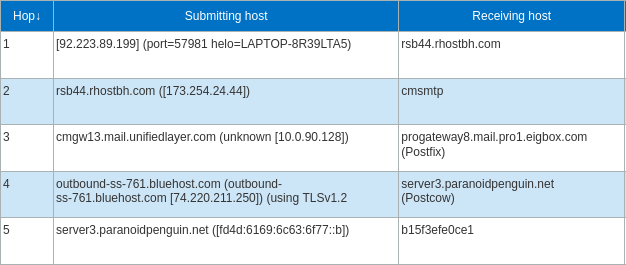
Message header analyzer from Microsoft.
The originating IP 92.223.89.199, has the following reverse DNS: 199.89.223.92.in-addr.arpa domain name pointer lux.lusobits[.]com. That domain has an interesting history, but let’s not dwell on that. Bluehost is the service provider responsible for accepting the email and delivering it to my inbox.
The URL shortener
Pxlme[.]me is the provider of the URL shortener that allows the scammer to hide the true destination of the linked website. In this case, it forwards the recipient to the ominous-sounding coinbase.com.compliance.esospro[.]net. This technique is popular for bypassing spam filters and other software responsible for keeping malicious content out of your inbox.
The phishing domain and website
The domain esospro[.]net is registered with Namecheap. The phishing website at coinbase.com.compliance.esospro[.]net. is hosted with Namecheaphosting.
The phishing website is apparently made by someone with less than stellar design and programming skills, and I believe most people will be able to avoid the scam.
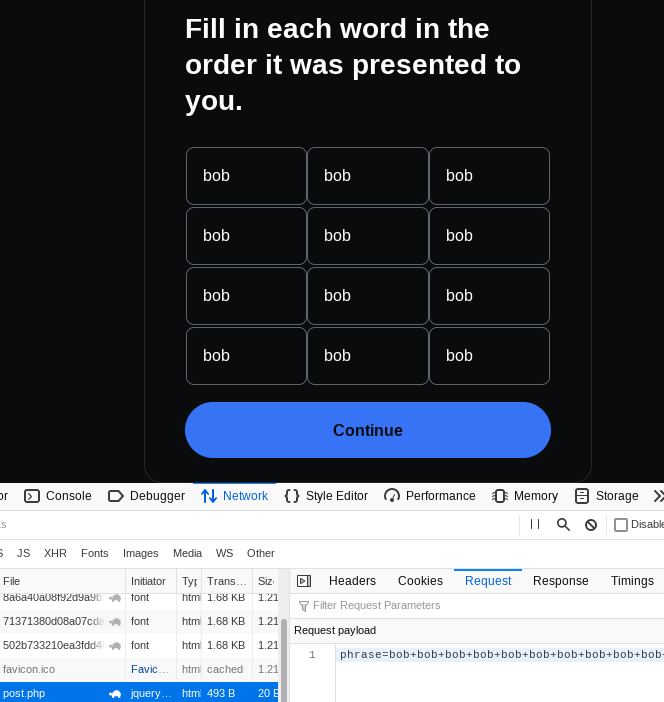
The phishing website attempting to steal a wallet seed phrase.
The SSL certificate issuer
The company responsible for issuing the SSL certificate for the domain coinbase.com.compliance.esospro[.]net is Sectigo Limited. The information is available from Certificate Transparency (CT) logs right here.
Authority Information Access:
CA Issuers - URI:http://crt.sectigo.com/SectigoRSADomainValidationSecureServerCA.crt
OCSP - URI:http://ocsp.sectigo.com
X509v3 Subject Alternative Name:
DNS:coinbase.com.compliance.esospro.net
DNS:www.coinbase.com.compliance.esospro.net
Apparently, someone paid to have this certificate issued.
The takedown attempt
The following companies are providing services for the scammer, likely without their knowledge or consent.
- Bluehost (email service)
- PixelMe (redirection service)
- Namecheap (domain and hosting services)
- Sectigo Limited (SSL certificate issuer)
The good news is that I have taken it upon myself to report my finding to each of these service providers, as this behavior is a clear violation of their terms of service. If only one of these companies takes action, the whole scam attempt would collapse like a house of cards.
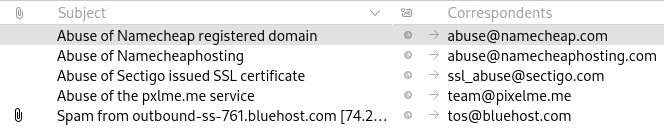
A list of abuse reports sent to relevant service providers (as of 2022-11-26).
The waiting game
Let’s see if any of these providers get back to me, or even better, pulls the plug on the scammer. So far, I’ve only gotten an autoreply from Namecheap. The other service providers have so far not even acknowledged my report. Am I just wasting my time by reporting criminal conduct on the interwebs again, or will I be pleasantly surprised? I’ll post an update next Saturday to let you know if anyone came to the aid of Joe Nobody.
